Personal Data vs Sensitive Data
Most organisations don’t fail data protection audits because they ignore the law.
They fail because they don’t understand what kind of data they are actually holding.
In our audits, we repeatedly see one dangerous assumption:
“If we protect all data the same way, we’ll be safe.”
That assumption is wrong—and regulators know it.
This blog breaks down personal data vs sensitive data, using real operational examples, clear comparisons, and a practical enforcement blueprint you can actually implement.
Why Does the Difference Between Personal Data and Sensitive Data Matter?
The difference between personal data and sensitive data determines how strong your security controls must be, how fast you must respond to breaches, and how severe penalties can become. Regulators evaluate whether protections are proportionate to data risk. Treating all data equally signals poor governance, not caution.
This isn’t semantics.
It’s risk math.
If sensitive data leaks, harm is immediate and irreversible.
If personal data leaks, impact may be contextual and containable.
And regulators penalise based on impact potential, not volume.
What Is Personal Data?
Personal data is any information that can identify an individual, directly or indirectly. Regulators interpret identification broadly—covering digital identifiers, behavioural signals, and metadata. If data can single out a person once combined with other datasets, it qualifies as personal data.
Legal definition aside, here’s the operational test:
Can your system point to a specific individual?
If yes, you’re handling personal data.
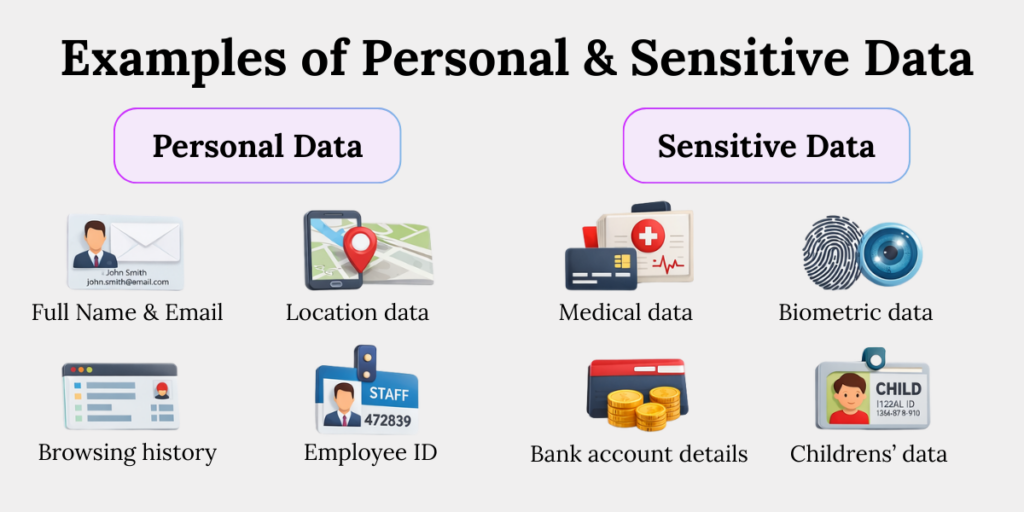
Personal Data: Real-World Examples You Already Handle
| Scenario | Why It’s Personal Data |
| Customer name + phone number | Direct identification |
| Email address alone | Uniquely identifies a person |
| IP address + device ID | Indirect but linkable |
| Employee ID mapped to HR records | Identifiable internally |
| Website cookies tied to behaviour | Digital fingerprint |
Personal data often starts harmless and becomes risky when systems integrate. This is where most organisations lose visibility.
What Makes Data “Sensitive” ?
Sensitive data is personal data that can cause significant harm if misused—financial, physical, reputational, or discriminatory. Regulators require stronger safeguards because breaches involving sensitive data create irreversible consequences, not just inconvenience.
Basically, sensitive data is personal data plus higher harm potential.
Sensitive data is not “more private.”
Think of it as data that can be weaponised.
Sensitive Data: Practical Examples Across Industries
| Industry | Sensitive Data Example | Why It’s High Risk |
| BFSI | Bank account numbers | Enables fraud |
| Healthcare | Medical diagnoses | Leads to discrimination |
| HR | Biometric attendance data | Permanent identifiers |
| Education | Children’s Aadhaar data | Identity theft risk |
| Telecom | Call detail records | Surveillance exposure |
What is the Difference Between Personal & Sensitive Data?
The difference between personal data and sensitive data lies in risk and impact. Personal data requires standard, baseline safeguards. Sensitive data carries a higher potential for harm and therefore demands stronger security controls, tighter access restrictions, and faster breach escalation. Applying uniform protection signals weak, non–risk-based governance to regulators.
Here’s the distinction most policies fail to operationalise.
Side-by-Side Compliance Expectations
| Area | Personal Data | Sensitive Data |
| Encryption | Standard encryption to prevent casual or unauthorised access. Suitable for data like names, emails, and phone numbers. | Strong encryption or tokenisation so data is unreadable even if systems are breached. Expected for financial, health, biometric, or identity data. |
| Access Control | Role-based access where employees can view data needed for their job. Access is broader but still controlled. | Least-privilege access where only a small, clearly defined group can view or process the data. No convenience-based access allowed. |
| Logging | Basic logs that record who accessed the data and when. Used mainly for audits and reviews. | Continuous, tamper-evident logs that cannot be altered. Used to detect misuse, insider threats, and unauthorised access in real time |
| Monitoring | Periodic reviews to ensure data is not misused over time. Issues are usually identified after the fact. | Real-time monitoring with alerts so suspicious activity is detected immediately, not weeks later. |
| Breach Response | Impact is assessed first to decide if escalation or notification is required. Response timelines are more flexible. | Immediate escalation is expected because misuse can cause serious harm. Delays are viewed as governance failures by regulators. |
Hard truth:
If your organisation applies the personal data approach to sensitive data, regulators see under-protection.
If you apply the sensitive data approach to all data, operations break.
Why Misclassification is Dangerous?
Most compliance failures happen because organisations document classifications but don’t enforce them technically. Regulators penalise this “policy-system gap” because it shows lack of operational control, not lack of awareness.
We see the same failure patterns repeatedly.
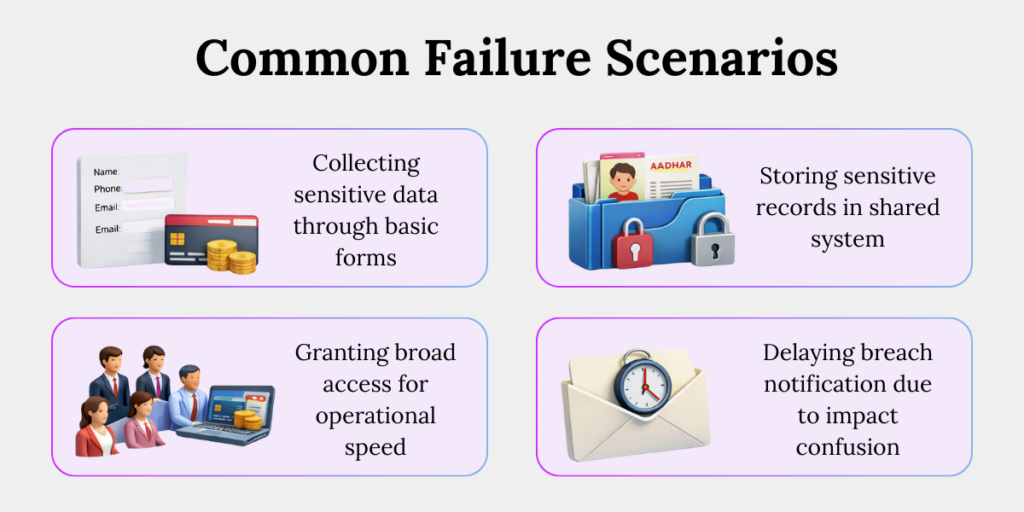
Common (and Costly) Failure Scenarios
1. Collecting Sensitive Data Through Basic Forms
Sensitive information is often captured using generic forms meant for names and contact details. This leads to stronger data being stored without enhanced controls, encryption, or consent discipline—creating immediate compliance gaps.
2. Storing Sensitive Records in Shared Systems
Sensitive data is frequently saved in shared drives, CRMs, or ticketing tools for convenience. These systems are rarely designed for high-risk data, making unauthorised access and internal misuse difficult to detect.
3. Granting Broad Access for Operational Speed
To avoid delays, organisations give multiple teams access to sensitive data. This breaks the principle of least privilege and exposes high-risk data to unnecessary internal users, a red flag during audits.
4. Delaying Breach Notification Due to Impact Confusion
When data isn’t clearly classified, teams struggle to assess breach severity. This causes delays in escalation and notification, which regulators interpret as poor governance—not uncertainty.
This isn’t malicious behaviour.
It’s architectural neglect.
And regulators no longer excuse it.
Practical Blueprint: How to Classify and Enforce Data Correctly
Effective compliance requires building classification into systems, not documents. Maintain a live data inventory, tag data by sensitivity at entry, and automate controls accordingly. Classification without enforcement is performative compliance.
Here’s what actually works.
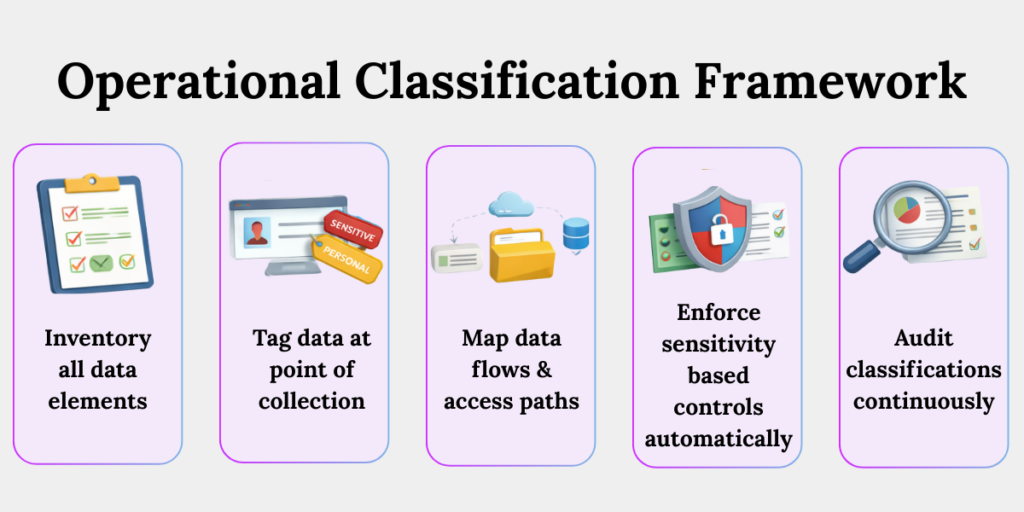
The Operational Classification Framework
1. Inventory All Data Elements
Create a complete list of personal and sensitive data across applications, databases, cloud tools, and third-party vendors. Without a live inventory, compliance decisions are based on assumptions, not evidence.
2. Tag Data at the Point of Collection
Classify data as personal or sensitive when it first enters your systems. Early tagging ensures the right controls are applied immediately, rather than retrofitted after risk exposure.
3. Map Data Flows and Access Paths
Track where each data type travels, who can access it, and where it is stored. This visibility is critical for enforcing purpose limitation and responding accurately during incidents.
4. Enforce Sensitivity-Based Controls Automatically
Apply security, access, and monitoring controls programmatically based on data classification. Manual enforcement fails at scale and is not defensible during regulatory reviews.
5. Audit Classifications Continuously
Revalidate data classifications whenever systems change, vendors are added, or processing purposes evolve. Data risk is dynamic, and static classification quickly becomes non-compliant.
How Correct Classification Reduces Regulatory and Business Risk
Accurate classification limits blast radius during incidents, simplifies regulatory explanations, and demonstrates accountability. Regulators assess whether risk was anticipated and controlled—not whether incidents were avoided entirely. Preparedness mitigates penalties.
Here’s how proper classification translates into real regulatory and business advantages
1. Limits Incident Blast Radius
When data is correctly classified, teams know immediately what type of data is affected during an incident. This prevents overreaction, reduces unnecessary shutdowns, and confines damage to the smallest possible scope.
2. Enables Faster, Defensible Decisions
Clear classification removes guesswork during breach assessment and escalation. Teams can act decisively because controls, response paths, and notification thresholds are already defined by data sensitivity.
3. Demonstrates Accountability to Regulators
Regulators look for evidence that risk was anticipated and managed deliberately. Sensitivity-based controls show that the organisation understood potential harm and built protections accordingly.
4. Reduces Penalty Exposure
Preparedness matters more than perfection. When controls align with data risk, regulators are more likely to view incidents as managed failures rather than governance breakdowns.
5. Strengthens Business Continuity
Accurate classification prevents unnecessary operational disruption. Critical systems handling low-risk personal data can continue functioning while sensitive data incidents are isolated and resolved.
Conclusion
Compliance isn’t about protecting everything the same way.
It’s about protecting the right data, the right way.
Personal data needs governance, and sensitive data needs containment.
If your systems can’t tell the difference, regulators will—during audits, investigations, or breach reviews.
Classify intentionally. Enforce relentlessly.
That’s how a real compliance fortress is built.
Key Takeaways
- Most compliance failures start with misclassification, not ignorance of the law.
- Personal data and sensitive data carry different risk levels and must be protected differently.
- Personal data identifies individuals, while sensitive data can cause serious harm if misused.
- Regulators expect risk-based controls, not uniform protection across all data types.
- Misclassification leads to real operational failures, from excessive access to delayed breach response.
- Policies alone don’t protect data—systems must enforce classification in practice.
- A live data inventory and sensitivity-based controls are the foundation of defensible compliance.
- Correct classification reduces penalties, limits incident impact, and strengthens business continuity.



