Why DPDP Matters to Education Sector
Educational institutions sit on a goldmine of personal data – student records, Aadhaar copies, health details, behavioural analytics from EdTech platforms. Under the Digital Personal Data Protection Act, 2023 (DPDP Act), that goldmine is also a regulatory minefield.
The question is not whether schools, colleges, and universities are covered. They are.
The real question is: Are you architecting a fortress—or storing student data in scattered spreadsheets and hoping nothing breaks?
Let’s build the shield properly.
Does DPDP Apply to Education Sector?
Yes. DPDP applies to schools, colleges, universities, coaching institutions, and EdTech platforms because they determine the purpose and means of processing student personal data. Under the Digital Personal Data Protection Act, 2023, such institutions qualify as “Data Fiduciaries,” triggering obligations under Rules 6 (security), 7 (breach notification), and 10 (children’s data).
Under Section 2(i) of the Act, a Data Fiduciary is any entity that determines how personal data is processed.
Translation? If you decide why and how student data is used, you are the bank manager of that information.
Now consider the risk layers:
1. Children’s data (Rule 10):
Requires verifiable parental consent; prohibits tracking, behavioural monitoring, and targeted advertising.
2. Security safeguards (Rule 6):
Mandates encryption, access controls, logging, and 1-year log retention.
3. Breach notification (Rule 7):
Requires informing Data Principals “without delay” and reporting to the Data Protection Board within 72 hours.
4. Retention discipline (Rule 8):
Data cannot be stored indefinitely “just in case.”
That is not a compliance issue. It is a structural weakness.
Why DPDP Matters to Education Sector?
DPDP matters to the education sector because institutions predominantly process children’s personal data, which attracts stricter consent, tracking, and profiling restrictions under Rule 10.
The law also shifts compliance from paperwork to system-level controls, meaning schools must operationalize security, retention, and breach response—not merely draft privacy policies.
Data in education is deeply personal. Academic performance. Medical conditions. Family income details. A leak is not just a technical failure—it is a lifetime digital footprint.
Here is why this sector is uniquely exposed:
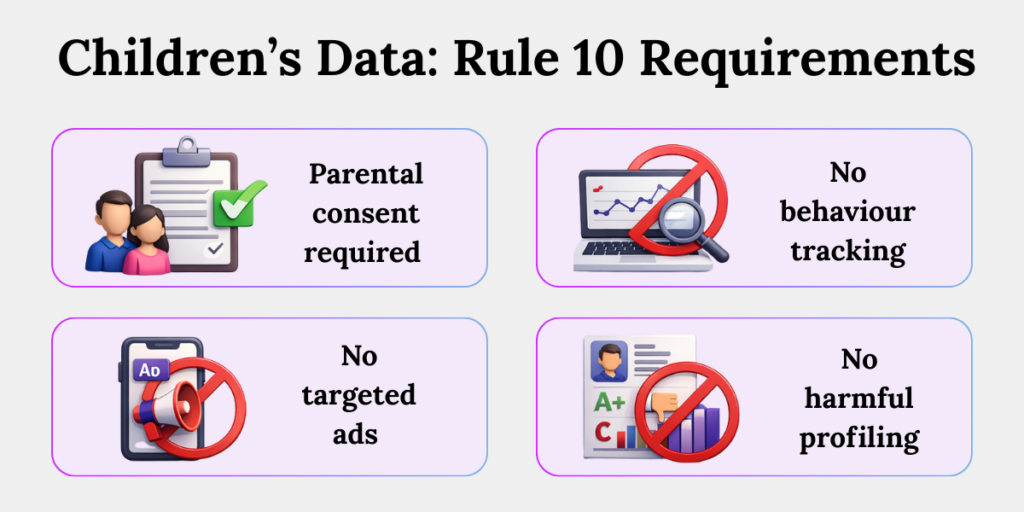
1. Children’s Data Is a High-Risk Category
Under Rule 10:
A. Obtain Verifiable Parental Consent
Schools must secure clear, verifiable consent from parents before processing a child’s data. A checkbox buried in an admission form is not enough. Consent must be informed, recorded, and retrievable.
B. Prohibit Behavioural Tracking
Tracking student activity across platforms for analytics or performance scoring can cross regulatory lines. If your LMS tracks browsing patterns beyond academic needs, you must review that configuration immediately.
C. Prohibit Targeted Advertising
Using student data for targeted ads—whether through third-party EdTech integrations or internal campaigns—is restricted. Education is not a marketing funnel.
D. Avoid Harmful Profiling
Automated profiling that labels students based on behaviour, grades, or socio-economic data can create bias. DPDP expects institutions to prevent decisions that may harm a child’s interests.
Most LMS systems and EdTech tools run behavioural analytics by default. Are you reviewing those configurations? Or trusting vendor dashboards blindly?
2. Data Volume Is Structurally High
Educational institutions process admission forms, academic records, health disclosures, CCTV footage, biometric attendance logs, financial aid details, and hostel surveillance records—creating a broad, layered attack surface across physical and digital systems.
3. Data Volume Is Structurally High
When a hospital suffers a breach, patients worry.
When a school suffers a breach, parents escalate.
In our observation, incidents involving minors trigger significantly higher reputational backlash due to public sensitivity around children’s privacy. That reputational multiplier is not written into the Act—but it is very real.
What Happens if Schools Ignore DPDP?
Failure to implement reasonable security safeguards (Rule 6) can attract penalties up to ₹250 crore. Failure to notify breaches under Rule 7 can attract penalties up to ₹200 crore. Violations related to children’s data under Rule 10 can attract penalties up to ₹200 crore. Enforcement under Section 33 evaluates severity, duration, and mitigation efforts.
This is not symbolic legislation.
Section 33 requires:
- Reasoned orders.
- Opportunity to be heard.
- Assessment based on duration, mitigation efforts, and harm caused.
In short: enforcement will evaluate your architecture—not your intent.
How Can Educational Institutions Become DPDP Compliant?
Educational institutions must implement a four-part compliance framework: data visibility, purpose enforcement, security safeguards, and breach readiness. These translate legal obligations under the DPDP Act into operational systems. Institutions that embed compliance into workflows—not just policies—reduce both regulatory exposure and reputational risk.
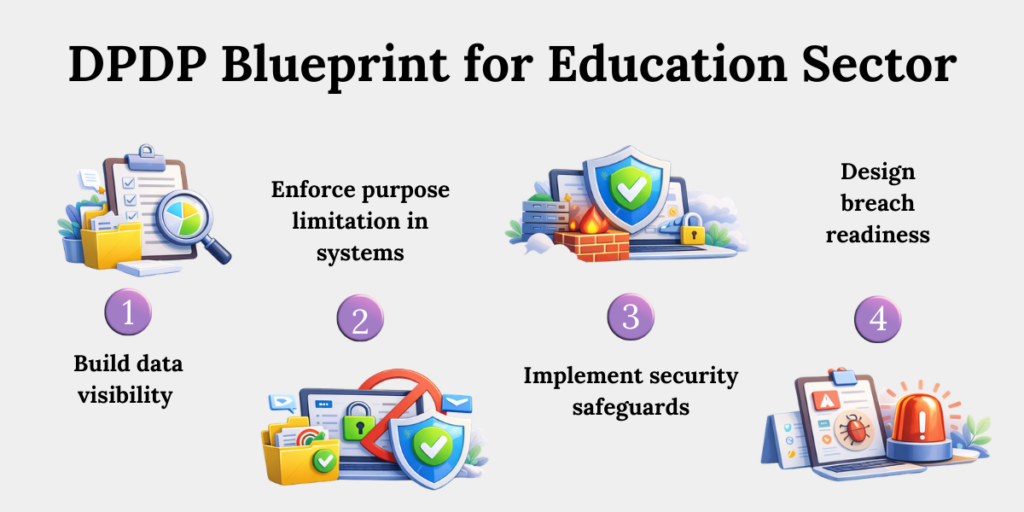
Compliance is a fortress. Let’s design it.
1. Build Data Visibility (Inventory + Mapping)
Start here. Always.
Without a live data inventory, your institution is defending blind corridors.
a. Map All Processing Activities
Document where student data enters your systems—admissions, exam portals, transport tracking, hostel management. If you cannot list it, you cannot protect it.
b. Classify Data Types Clearly
Separate children’s data, health data, financial data, and general personal data. Classification determines risk level and control intensity.
c. Identify Third-Party Access
List every vendor—LMS providers, payment gateways, cloud storage platforms. Many breaches originate from vendor misconfigurations, not internal staff.
d. Document Cross-Border Transfers
Check if student data is stored on foreign servers. Rule 15 permits transfers unless restricted—but institutions must verify hosting arrangements.
e. Define Retention Timelines
Delete alumni data when no longer required. Archiving everything “just in case” is not strategy—it is liability.
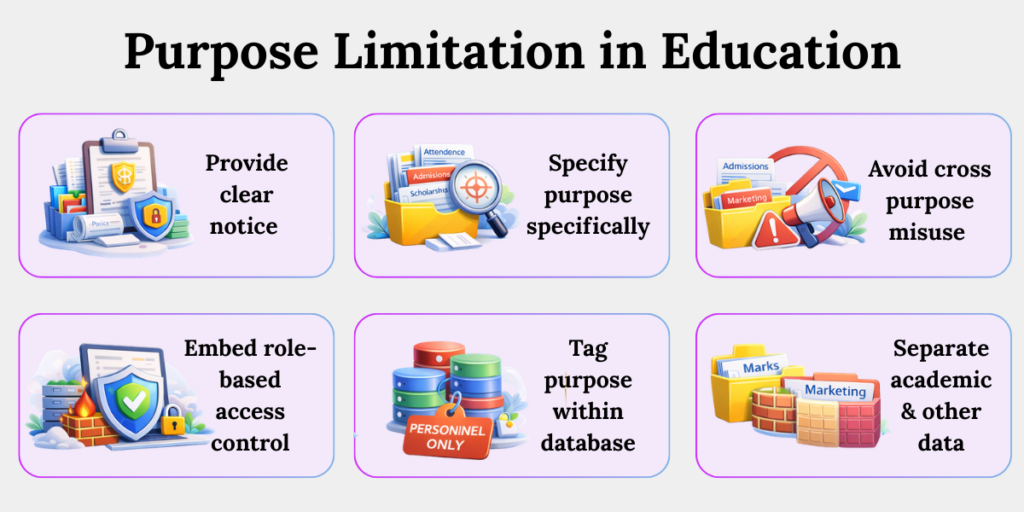
2. Enforce Purpose Limitation in Systems
Policy statements are decorative. System controls are defensive walls.
a. Provide Clear Notice
Explain exactly why data is collected—admissions, attendance, scholarships. Vague phrases like “administrative purposes” will not survive scrutiny.
b. Specify Purpose Precisely
Define whether biometric data is for attendance only—not analytics, not behaviour scoring. Precision limits misuse.
c. Avoid Cross-Purpose Reuse
Do not reuse admission data for alumni marketing campaigns without fresh consent. Convenience is not compliance.
Do not reuse admission data for marketing campaigns without fresh consent. It is tempting. It is also risky.
d. Embed Role-Based Access Controls (RBAC)
Limit who can access health records versus academic scores. A teacher does not need financial aid data access.
e. Tag Purpose Within Databases
Label datasets by intended use. When systems enforce purpose tagging, accidental misuse drops significantly.
f. Segregate Academic and Marketing Data
Maintain separate environments. Mixing both is like storing exam papers and promotional flyers in the same locker.
Break the data hoarding habit. Archive what you do not need.
3. Implement Security Safeguards (Rule 6)
Security is not optional. It is mandatory architecture.
a. Encryption and Masking
Encrypt student databases so that even if servers are compromised, the data remains unreadable. A stolen encrypted file is far less damaging than an open Excel sheet of marks.
b. Access Controls
Implement login restrictions and multi-factor authentication. In several breaches we reviewed, shared admin passwords were the weakest link.
c. Logging and Monitoring
Track who accessed what data and when. If a staff member downloads 5,000 student records at midnight, your system should flag it.
d. Backups and Recovery Testing
Maintain offline backups. Ransomware often locks live systems; tested backups ensure classes resume without weeks of disruption.
e. Minimum 1-Year Log Retention
Retain logs long enough to investigate delayed complaints. Without logs, proving compliance becomes guesswork.
Audit system logs quarterly. Test backups. Conduct vulnerability assessments.
Build redundancy before attackers test it for you.
4. Implement Security Safeguards (Rule 6)
DPDP requires notifying affected individuals “without delay” and reporting to the Data Protection Board within 72 hours. Institutions must disclose the nature of the breach, categories affected, likely consequences, and mitigation measures.
You do not build a fire exit during a fire.
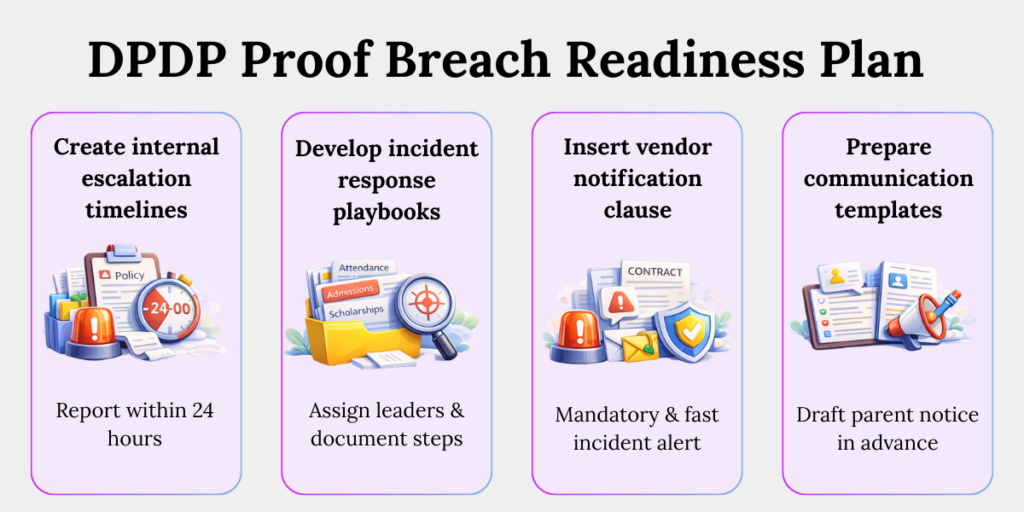
a. Create Internal Escalation Timelines
Ensure staff report suspected breaches within 24 hours internally. Delay often begins at the bottom of the chain.
b. Develop Incident Response Playbooks
Define who investigates, who communicates, and who documents. Confusion during a breach amplifies damage.
c. Insert Vendor Notification Clauses
Mandate vendors to inform you immediately of incidents. Many institutions discover vendor breaches weeks later.
d. Prepare Communication Templates
Draft parent notification formats in advance. Clear, calm communication prevents rumour-driven panic.
Speed preserves credibility.
Conclusion
DPDP is not a bureaucratic hurdle. It is a structural reset for how educational institutions handle student data.
If you process admissions, attendance, health records, or biometric logs—you are already within its scope. The only question is whether your systems reflect that reality.
Education officers, principals, and trustees—this is your moment to act. Audit your data architecture. Engage compliance experts. Transform policies into operational controls.
Because protecting student data is no longer optional. Under DPDP, it is a legal mandate—and a leadership responsibility.
Key Takeaways
- DPDP applies to the education sector because schools and colleges qualify as Data Fiduciaries handling student personal data.
- Children’s data attracts stricter obligations including parental consent, anti-tracking rules, and profiling restrictions under Rule 10.
- Educational institutions process high volumes of sensitive data, creating a broad and layered attack surface.
- Reputational risk is amplified in education, especially when minors’ data is involved.
- Ignoring DPDP can trigger penalties up to ₹250 crore, with enforcement focused on system-level safeguards.
- Data visibility through inventory and mapping is the foundation of compliance.
- Purpose limitation must be enforced within systems—not just written in policies.
- Security controls and breach readiness determine whether an institution survives a regulatory incident.