The DPDP Compliance Checklist: A 7-Step Operational Blueprint
Regulatory ambiguity is expensive.
Under India’s Digital Personal Data Protection (DPDP) Act, 2023, penalties for a single instance of non-compliance can reach ₹250 crore—a threshold that fundamentally changes how organisations must approach data governance.
But the real risk is not the fine alone.
The financial penalty is only the visible impact; the deeper damage comes from operational chaos after a breach, prolonged regulatory scrutiny, and irreversible erosion of customer trust.
That is why DPDP compliance cannot be treated as a checkbox exercise. It must be built as a defensive architecture—a compliance fortress—designed intentionally, tested continuously, and governed from the top.
The 7-Step DPDP Compliance Checklist
This DPDP checklist operationalises compliance into seven sequential controls:
- Data inventory
- Data mapping
- Consent management
- Privacy notices
- DPIAs
- DPO-led governance
- Continuous monitoring
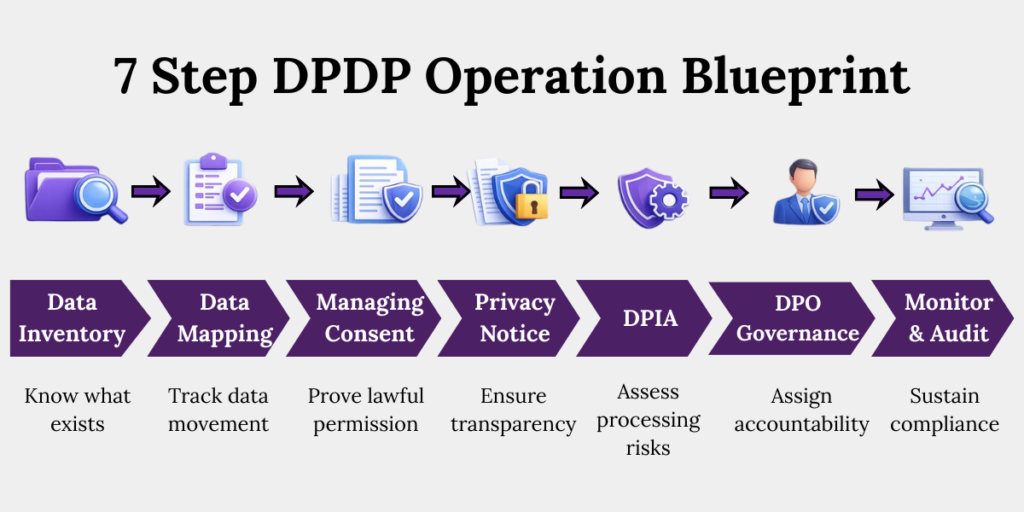
Together, these steps create demonstrable compliance under the DPDP Act, reduce breach impact, enable Data Principal rights, and convert regulatory obligations into a scalable governance framework.
Data Inventory: Defining What You Actually Possess
A data inventory is the foundation of DPDP compliance. It identifies every category of personal data an organisation collects, where it is stored, who owns it, and why it exists. Without this visibility, security controls, consent enforcement, retention, and breach response become guesswork rather than governance.
A Data Inventory answers one critical question:
What personal data do we actually have?
In practice, organisations consistently underestimate their exposure. In our audits, we frequently observe forgotten marketing databases, archived HR folders, unused SaaS tools, and shared drives holding sensitive personal data. These are not malicious failures—they are operational drift.
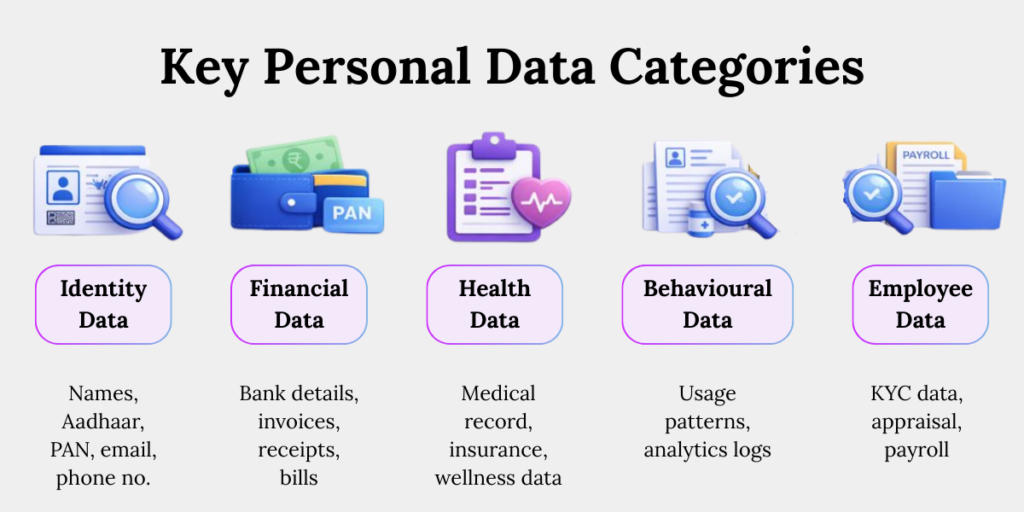
Key Personal Data Categories to Inventory
1. Identity Data
Includes names, Aadhaar, PAN, email addresses, and phone numbers. This data directly identifies individuals and is often scattered across onboarding forms, CRM systems, and support databases.
2. Financial Data
Covers bank details, salary records, invoices, and transaction logs. Financial data carries higher breach impact and stricter security expectations under DPDP.
3. Health Data
Includes medical records, insurance documents, diagnostic reports, and wellness data. Even limited exposure can trigger severe harm and regulatory scrutiny.
4. Behavioral Data
Comprises usage patterns, analytics logs, clickstreams, and interaction histories. Often underestimated, this data enables profiling and requires purpose control.
5. Employee Data
Includes KYC documents, payroll files, appraisal records, and internal identifiers. Employee data is personal data and fully covered under DPDP.
Where Personal Data Typically Resides
1. Cloud Platforms (AWS, Azure, GCP)
Primary storage for databases, backups, and analytics workloads. Misconfigured access controls are a common exposure point.
2. SaaS Tools (CRM, HRMS, Marketing Platforms)
Third-party tools often store more personal data than organisations realise, including historical exports and inactive user data.
3. On-Premises Servers
Legacy systems, file servers, and local databases often escape modern security monitoring but still process personal data.
4. Vendor Systems
Payment processors, payroll vendors, IT support partners, and consultants may hold full or partial copies of personal data.
5. Physical Archives
Paper records, storage rooms, and offsite archives still qualify as personal data repositories under DPDP.
Every data category must have a designated custodian accountable for its lifecycle.
The final step is data minimisation—removing redundant, obsolete, and trivial data. If data serves no lawful purpose, it represents 100% liability and 0% business value.
A data inventory is not documentation—it is your visibility layer. You cannot defend what you cannot see.
Data Mapping: Understanding How Data Moves
Data mapping visualises how personal data flows across systems, teams, and vendors from collection to deletion. Under DPDP, this visibility is essential to honour Data Principal rights, enforce retention, and respond to breaches within statutory timelines. Without a data map, compliance actions become slow, fragmented, and unreliable.
If inventory answers what, data mapping answers how.
A Data Map traces the lifecycle of personal data across your organisation—like a plumbing diagram for your data ecosystem.
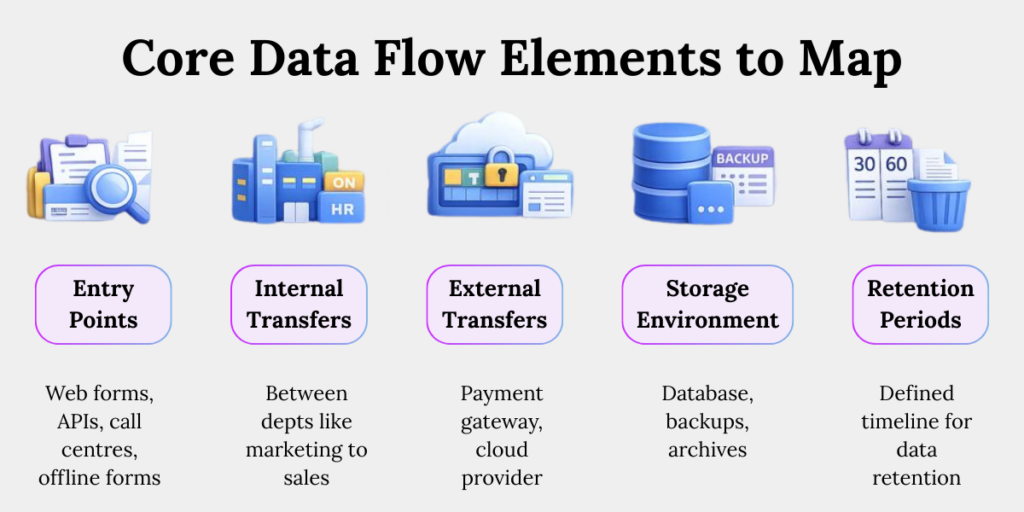
Core Data Flow Elements to Map
1. Entry Points
Web forms, APIs, mobile apps, call centres, and offline forms where personal data first enters your systems.
2. Internal Transfers
Movement of data between departments, such as marketing to sales or HR to payroll, often without documented purpose checks.
3. External Transfers
Sharing with payment gateways, cloud providers, consultants, or analytics vendors, each introducing third-party risk.
4. Storage Environments
Databases, backups, data lakes, shared drives, and archives where data resides during processing.
5. Retention Periods
Defined timelines for how long each data category is kept, aligned with purpose and legal requirements.
6. Disposal Mechanisms
Deletion, anonymisation, or destruction processes once retention periods expire.
Why this matters:
When a Data Principal requests access, correction, or erasure, you must know which system holds their data, which vendor has a copy, and whether deletion has already occurred. Without a data map, statutory timelines are impossible to meet.
Consent Management: Making Permission Verifiable
Under the DPDP Act, consent must be free, specific, informed, unconditional, and unambiguous—and provable. Consent systems must generate auditable evidence showing what was agreed to, when, for what purpose, and how withdrawal is enabled. Without verifiable consent logs, the legal basis for processing collapses.
Consent is not a UI checkbox. It is legal evidence.
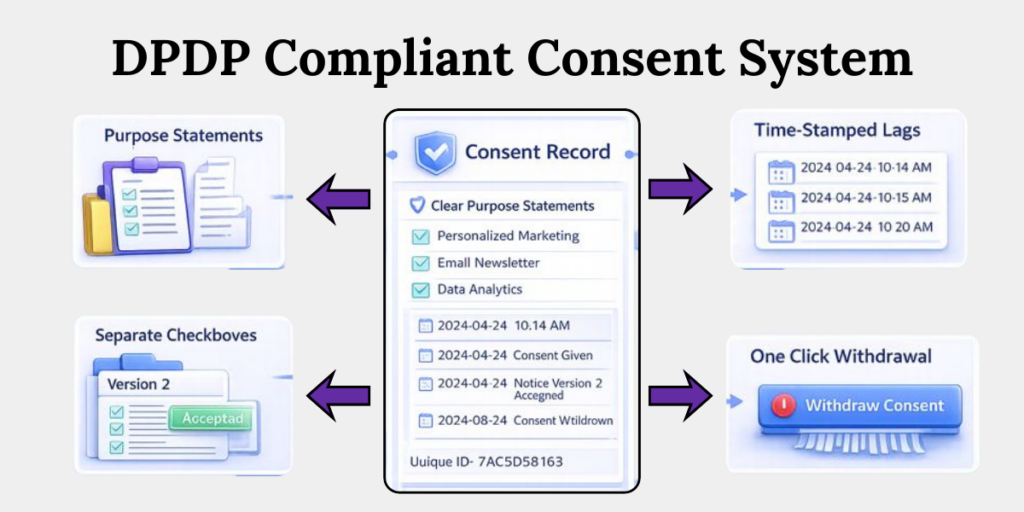
Elements of a DPDP-Compliant Consent System
1. Clear Purpose Statements
Each consent request must clearly state why data is collected, in simple language tied to a specific use.
2. Separate Checkboxes for Separate Purposes
Bundled consent invalidates choice. Marketing, analytics, and service delivery must be individually selectable.
3. Time-Stamped Logs
Every consent action must be logged with date, time, user identifier, and system reference.
4. Record of Notice Version Shown
You must retain the exact privacy notice version presented at the time consent was obtained.
5. One-Click Withdrawal Mechanism
Withdrawal must be as easy as giving consent. Delayed or manual withdrawal processes violate DPDP principles.
Consent also enforces purpose limitation. Data collected for OTP verification cannot be reused for marketing without renewed consent.
In enforcement scenarios, regulators first ask for consent logs. If you cannot produce them, your processing has no legal foundation.
Privacy Notice: The Public Contract
A privacy notice is a legally binding transparency document under DPDP. It must accurately reflect how personal data is collected, used, retained, and shared. Mismatches between notice and actual operations create direct non-compliance and reputational risk.
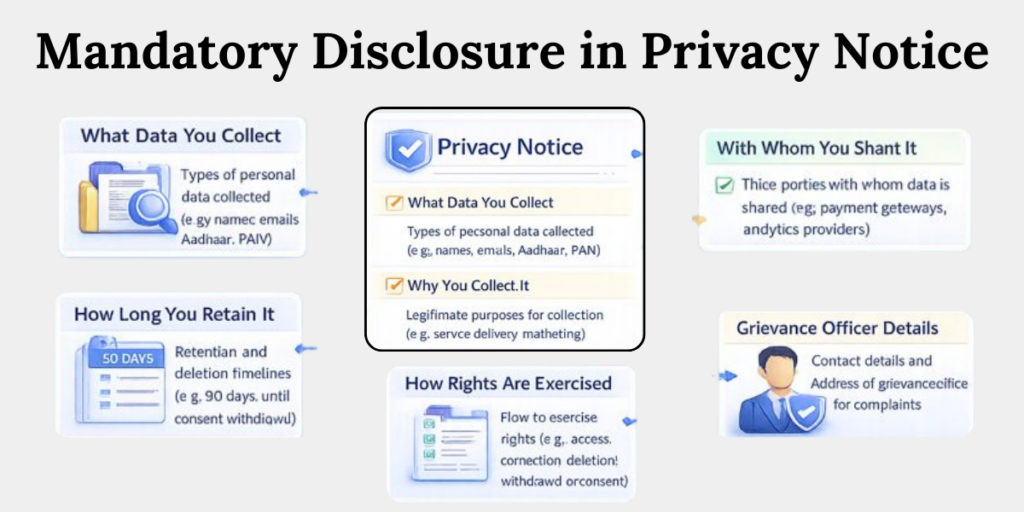
Mandatory Disclosures in a DPDP Privacy Notice
1. What Data You Collect
Clearly specify each category of personal data collected across products, platforms, and touchpoints. This includes identity, contact, financial, behavioral, employee, or sensitive data, as applicable.
2. Why You Collect It
Explain the exact purpose for each data category in plain language. Avoid broad phrases like “service improvement” unless clearly defined and linked to a lawful processing activity.
3. How Long You Retain It
State defined retention periods or the objective criteria used to decide deletion. Retention must be purpose-bound—data cannot be stored indefinitely without legal justification
4. With Whom You Share It
Disclose categories of third parties such as processors, vendors, service providers, or affiliates. Transparency must cover who receives the data and for what purpose, not just generic labels.
5. How Individuals Exercise Their Rights
Provide step-by-step instructions for exercising rights like access, correction, erasure, and grievance redressal. The process must be clear, accessible, and time-bound under DPDP requirements.
6. Grievance Officer Contact Details
Publish the name or designation of the Grievance Officer along with a valid contact mechanism. This enables Data Principals to raise concerns and is a mandatory statutory disclosure.
The notice must be available in English or any of the 22 Eighth Schedule languages upon request.
Most importantly, it must reflect operational reality, not aspirational policy.
DPIA: Risk Assessment Before Innovation
A Data Protection Impact Assessment (DPIA) identifies and mitigates privacy risks before launching high-risk processing activities. Mandatory for Significant Data Fiduciaries and critical for AI-driven systems, DPIAs embed privacy-by-design into innovation rather than retrofitting compliance after deployment.
High-Risk Scenarios Requiring DPIA
1. AI Profiling
Use of algorithms to analyse personal data and predict an individual’s behaviour, preferences, or characteristics. This can affect how people are evaluated, targeted, or treated, making risk assessment essential.
2. Large-Scale Behavioral Tracking
Continuous monitoring of users across websites, apps, devices, or services. When done at scale, this can reveal detailed patterns about individuals and significantly increase privacy risk.
3. Sensitive Data Processing
Processing health, biometric, financial, or children’s personal data. These data types carry higher harm potential if misused or breached and require stronger safeguards.
4. Automated Decision-Making
Systems that make decisions about individuals with little or no human involvement, such as eligibility checks or risk scoring. Errors or bias in such systems can directly impact individual rights.
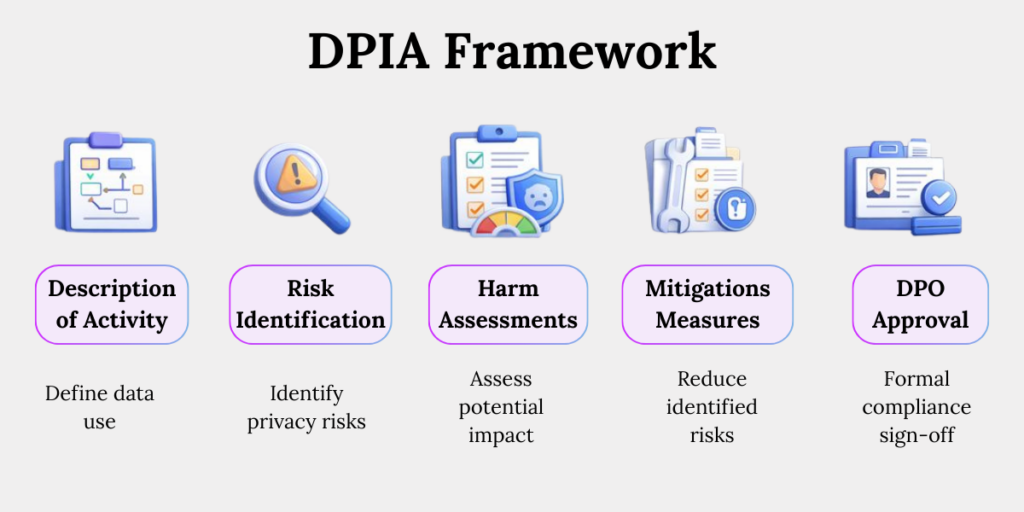
Core Components of a DPIA
1. Description of Processing Activity
Clearly explain what personal data is being processed, how it is collected and used, and the specific purpose behind the processing activity.
2. Risk Identification
Identify potential risks to privacy, data security, and individual rights that could arise from the processing, including misuse, unauthorised access, or loss of data.
3. Harm Assessment
Assess the possible impact on individuals if something goes wrong, such as identity theft, discrimination, profiling, or denial of services.
4. Mitigation Measures
Describe the safeguards put in place to reduce identified risks, such as encryption, data minimisation, access controls, or adding human oversight.
5. DPO Approval
Obtain formal sign-off from the Data Protection Officer confirming that risks have been reviewed, mitigation measures are adequate, and processing can proceed.
DPIAs convert compliance from reactive defence into proactive engineering.
DPO & Governance: Accountability at the Top
DPDP compliance requires formal governance led by a Data Protection Officer with authority, independence, and board-level access. Governance ensures privacy oversight is embedded into decision-making, breach response, and organisational culture—not delegated as an IT task.
Core Responsibilities of the DPO
1. Monitoring Compliance
Continuously oversee how the organisation handles personal data to ensure DPDP requirements are followed across teams, systems, and processes.
2. Handling Grievances
Receive and manage complaints from Data Principals, ensuring responses are accurate, timely, and within statutory timelines prescribed under the DPDP Act.
3. Coordination with the Data Protection Board
Act as the official point of contact with the Data Protection Board of India, including responding to queries, notices, or investigations.
4. Overseeing DPIAs
Review and approve Data Protection Impact Assessments for high-risk processing activities, ensuring risks are identified and mitigated before launch.
5. Ensuring Breach Response Protocols
Supervise breach detection, escalation, and response processes to ensure incidents are contained quickly and notifications are made as required
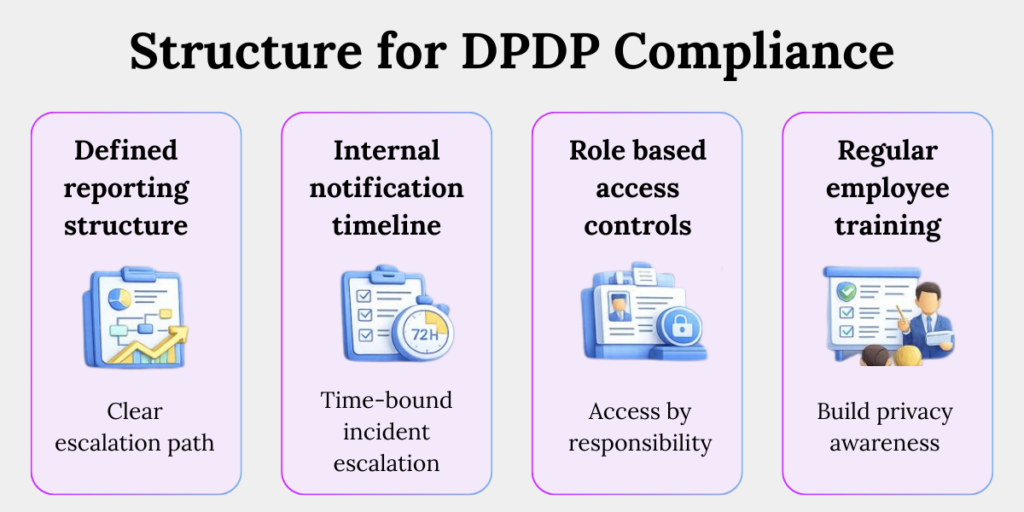
What Governance Structures Do You Need?
1. Defined Reporting Structures
Establish clear escalation paths so privacy risks, incidents, and decisions move quickly from operational teams to senior management and, where required, the Board.
2. Internal Breach Notification Timelines
Set predefined internal timelines (such as 72 hours) to identify, assess, and escalate potential data breaches before external notification obligations apply.
3. Role-Based Access Controls
Limit access to personal data based on job roles so employees can only view or use data necessary to perform their responsibilities.
4. Regular Employee Training
Conduct ongoing privacy and security training to reduce human error, improve awareness, and prevent accidental data leaks or phishing-related incidents.
The DPO must have authority. Governance without enforcement becomes symbolic.
Monitoring & Audit: Sustaining Compliance
DPDP compliance degrades without continuous monitoring. Regular audits, testing, and simulations ensure controls remain effective as systems, vendors, and personnel change. Sustained oversight prevents compliance decay and reduces breach impact when incidents occur.
Continuous Monitoring Activities
1. Annual Penetration Testing
Regularly test systems using real-world attack scenarios to check how well security controls prevent unauthorised access to personal data.
2.Vulnerability Scans
Continuously scan systems to identify security gaps such as misconfigurations, outdated software, or missing patches that could be exploited.
3. Quarterly Consent Log Audits
Review consent records to confirm that consent was validly obtained, withdrawals are honoured, and logs remain accurate and complete.
4. Vendor Risk Reviews
Periodically assess vendors and service providers to ensure they follow DPDP requirements and contractual data protection obligations.
5. Breach Simulation Drills
Run mock breach exercises to test response speed, internal coordination, and decision-making during high-pressure incidents.
6. Independent Data Audits (for SDFs)
Engage external auditors to provide independent assurance that DPDP compliance controls are operating effectively.
Without monitoring, compliance rusts.
Conclusion: From Obligation to Strategic Advantage
When implemented correctly, DPDP compliance evolves beyond regulatory defence into a strategic capability—strengthening customer trust, reinforcing investor confidence, improving operational clarity, reducing risk exposure, and creating durable competitive advantage.
Key Takeaways
- Data inventory creates visibility and accountability across all personal data.
- Data mapping enables rights fulfilment and breach readiness.
- Consent management must generate auditable legal evidence.
- Privacy notices must reflect real operational practices.
- DPIAs embed privacy-by-design into innovation.
- DPO-led governance anchors accountability at leadership level.
- Continuous monitoring prevents compliance decay.
- DPDP compliance, done right, becomes a business advantage—not a burden.



