Intimation of Personal Data Breach: Your Quick Response Guide
Introduction
In today’s digital ecosystem, personal data moves faster than ever across apps, cloud services, devices, and global networks. With this speed comes vulnerability.
Even the most secure organisations can face a personal data breach. What truly matters is how quickly and transparently they inform affected individuals and the regulatory authority.
Under the latest data protection regulations, Digital Personal Data Protection Act (DPDPA), the intimation of a personal data breach is not optional it is a legal obligation.
The moment a Data Fiduciary becomes aware of a breach, strict timelines and communication duties are triggered.
What Is a Personal Data Breach?
A personal data breach occurs when personal data is accidentally or unlawfully accessed, disclosed, altered, lost, or destroyed.
It covers hacking and ransomware, as well as everyday errors like sending data to the wrong person, unauthorised employee access, or misconfigured databases.
The moment the Data Fiduciary becomes aware of such an incident, the law requires immediate action.
Intimation to Affected Data Principals: Clear, Quick, and Meaningful
The first responsibility is towards the Data Principals, the individuals whose personal data has been compromised.
They must be informed as soon as possible and in a manner that is clear, concise, and easily understood.
The communication must be sent through the Data Principal’s registered mode of contact such as email, SMS, in-app notification, or user account alert.

To comply with the law, the notice must include five essential elements:
1. Description of the Breach
Data Fiduciaries must explain:
- What happened
- What type of personal data was affected
- How extensive the breach was
- When it occurred or was detected
This description should avoid technical jargon. Transparency helps individuals understand the seriousness of the situation.
2. Possible Consequences of the Breach
The Data Principal must be informed about the realistic risks that may arise from the breach.
These may include:
- Identity theft
- Financial fraud
- Account compromise
- Unauthorised access to personal profiles
- Misuse of sensitive information
Explaining consequences empowers individuals to take timely protective action.
3. Measures Taken by the Data Fiduciary
The organisation must share the immediate steps it has taken to contain the breach, such as:
- Blocking unauthorised access
- Securing compromised servers
- Resetting credentials
- Deploying cyber incident response teams
This demonstrates accountability and reassures affected individuals that the organisation is taking the action.
4. Recommended Safety Measures for the Data Principal
Data Principals must be guided on how they can protect themselves.
For example:
- Changing passwords
- Enabling multi-factor authentication
- Monitoring financial accounts
- Avoiding suspicious emails and messages
- Placing fraud alerts on their accounts
This step is crucial because the real impact of a breach often unfolds after the incident.
5. Contact Details for Assistance
The organisation must provide:
- A business contact person
- With clear contact information
- Who can respond to queries related to the breach
Clear communication lines ensure Data Principals feel supported and informed.
Intimation to the Data Protection Board: A Mandatory Requirement
Beyond informing individuals, the Data Fiduciary must also notify the Data Protection Board.
This ensures regulatory oversight and allows authorities to assess whether the breach was handled responsibly.
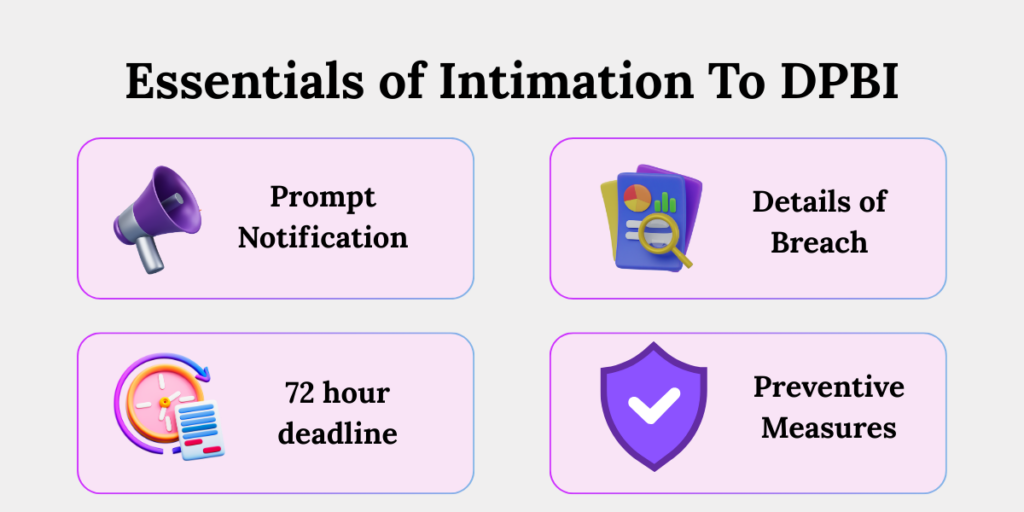
Initial Intimation Without Delay
Immediately upon becoming aware of the breach, the Data Fiduciary must share:
- The nature of the breach
- Its extent
- Its timing and location
- The likely impact
This early intimation helps the Board understand the severity of the incident from the start.
Detailed Report Within 72 Hours
Within 72 hours, or within an extended timeline approved by the Board, the Data Fiduciary must submit a comprehensive breach report.
This report must include:
1. Updated and Detailed Description
A more complete account of what happened, as investigations mature.
2. Events and Reasons Leading to the Breach
This covers:
- Technical causes
- Human errors
- Process failures
- Security gaps
Providing the root cause helps the Board evaluate systemic issues.
3. Measures Taken or Proposed to Mitigate Risk
This includes both:
- Immediate containment actions
- Future safeguards to prevent escalation
4. Findings on Who Caused the Breach
If available, the organisation must report:
- Whether the breach was caused by internal personnel
- External attackers
- Third-party vendors
- System vulnerabilities
5. Preventive Remedial Measures
The actions taken to ensure such a breach does not occur again such as policy changes, employee training, or infrastructure upgrades.
6. Confirmation of Intimations Sent to Data Principals
The Board must be updated on:
- How many individuals were informed
- How communication was sent
- What information was provided
This ensures compliance with transparency obligations.
Why Timely Intimation Matters
Protects Individuals
Data breaches can cause real harm financial loss, privacy invasion, reputational damage.
Early warning allows individuals to act before the impact grows.
Demonstrates Accountability
Transparent communication builds trust. No organisation is immune to breaches, but responsible handling improves credibility.
Reduces Regulatory and Legal Risk
Delayed or incomplete intimation can result in:
- Penalties
- Investigations
- Compliance violations
- Reputational damage
Immediate intimation is not just a rule, it’s a protection mechanism for organisations.
Strengthens Internal Governance
Documenting and reporting breaches pushes organisations to improve:
- Cybersecurity practices
- Data-handling processes
- Employee awareness
- Vendor oversight
Conclusion
A personal data breach is a moment of truth for any organisation. Your response transparent, timely, and accountable determines whether trust is preserved or lost.
The law lays out clear obligations: inform affected individuals without delay and report to the Data Protection Board within strict timelines.
By following these requirements, Data Fiduciaries not only comply with regulations but also demonstrate a commitment to safeguarding personal data.
Key Takeaways
- Under the DPDPA, immediate intimation of data breach is a legal requirement.
- The intimation should include a brief description, containment actions, safety tips, and contact details.
- A detailed report must then be sent to the Board within 72 hours, explaining the cause, impact, mitigation measures, and long-term preventive actions.
- Timely and complete reporting protects individuals, builds trust, and reduces legal and regulatory risk.
- It also pushes organisations to strengthen their internal processes and security.